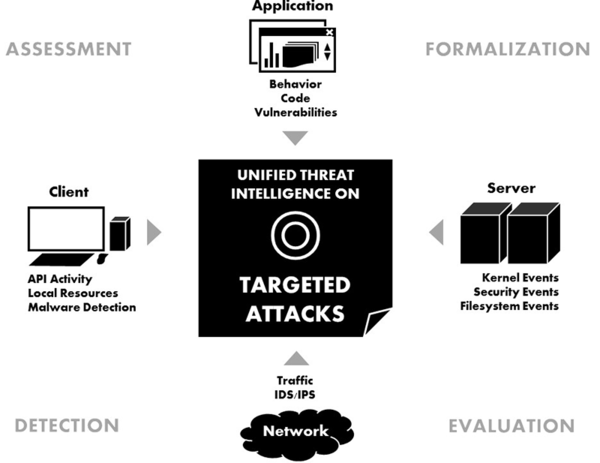
Research topics
The center aims at developing threat intelligence methodologies that observe the system as a whole and apply formal modeling in conjuncture with the collection, processing, comparison, and analysis of system state information. Its research topics are:
Formal methods
Next to extracting various attack indicators, we aim to develop a universal model for describing malicious behavior.
Behavioral analysis
Our applied work focuses on behavioral analysis of IT system activity and malicious software on API call level.
Data mining
Anomaly detection and threat response is enabled by data mining procedures utilizing a multitude of algorithms.
Honeypot & kernel monitoring
We use honeypot and kernel monitoring technology to tempt attackers and learn about APT behavior.